How I got a trip to amsterdam through bug bounty

So without wasting time lets move forward, Here I would like to share how I got a trip to Amsterdam with all expenses paid for 5 days.
At this moment a majority of them would have thought the Vulnerability would be a server-side issue, but Unfortunately, its a simple Vulnerability leading to full account takeover. The vulnerability was in the login portal, I guess some of you are familiar with this vulnerability.
First of all, let me tell you about this vulnerability which I like very much because it pays good enough & I have found it many times in different ways and the vulnerability is Full Account takeover, Account takeover can be through any method we just need to take over the account in any possible way, here the account takeover was done by Brute force on login portal. Now, what is it and how to find it?
For those who don’t know what Brute force attack is?
Brute force is a way of trying to bypass the login form or it might be any other form which needs a password to open that file or system. In simple words, we can say it’s just the process of guessing the password.
Here what I did was I created an account and was just checking for its requests and responses by intercepting the request through burpsuit, after some time checking for the minor vulnerabilities, I went to the forgot password page. Now the real problem was here when I was requesting a password for my account the server was by default setting a new password for my account and sending it to me via mail. When I received mail I saw the password was in a format such as
“Ab3CdF”
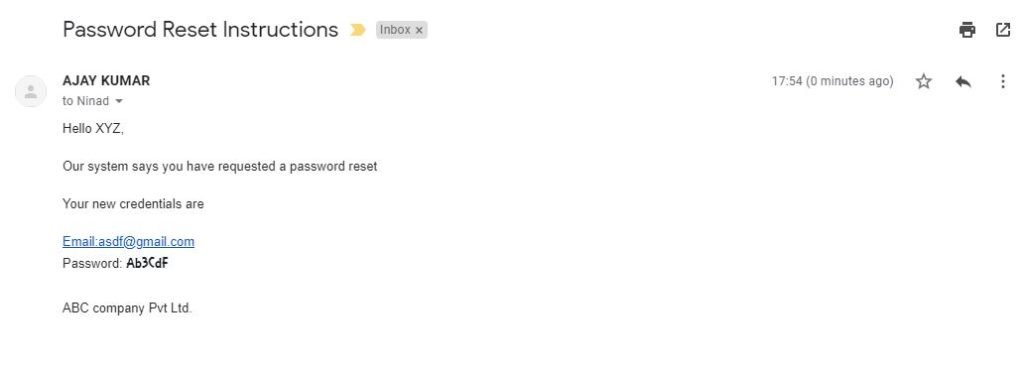
and it was a 6 digit password, to reconfirm the combination I requested the password for 100 times by this I got to know that there is no rate limiting implemented on the login page and forgot password page, Now we have the format of the password and nobody is gonna check us if we use it for brute forcing the account but it’s a 6 words password still we get a hell lot of passwords and its nearly (56,800,235,584) this much, now it’s really a lot of passwords for checking one account but we have the password format, So Here we can write a python script for generating the password or there are many other tools which will do the work for you. Thus once we generate the passwords we can use the burp-suit intruder (some thing like this)
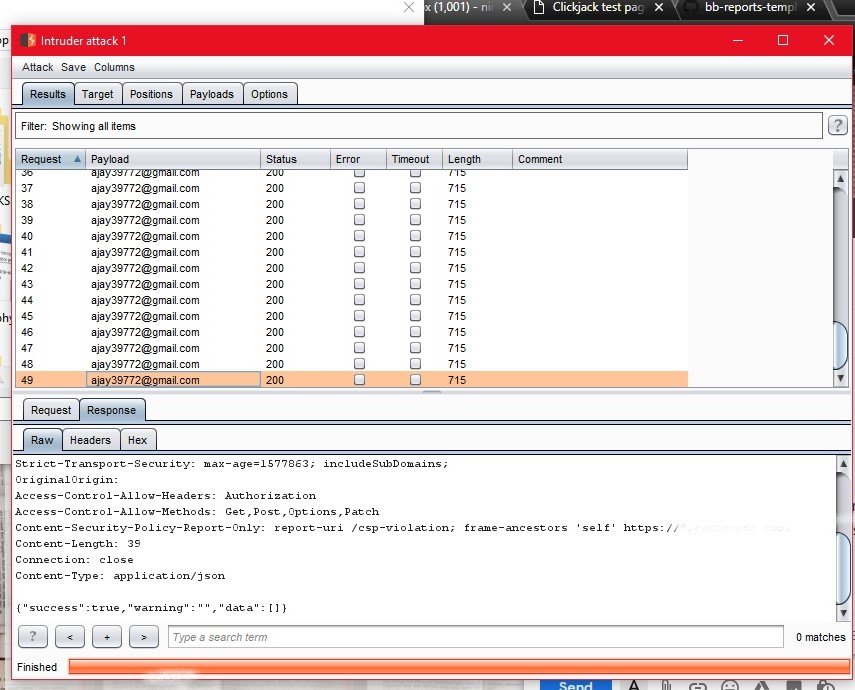
to carry out the brute force attack. Thus this leads to Full account takeover.
Thus this was all about this Vulnerability. There are many other ways for full account takeover and I guess this is the easiest one to understand,
I will be writing blogs, one by one on various ways to take over the account and my other bug bounty experiences. so this is it for the day, thank you for reading the blog. Meet you soon with something more exciting things in bug bounty/ penetration testing.




