All about SSL pinning bypass!
Hello people, hope you are doing good and playing well with security!
Today I am here again with a topic known as SSL pinning
What is it?
According to google its something like
“Pinning is an optional mechanism that can be used to improve the security of service or site that relies on SSL Certificates. Pinning allows you to specify a cryptographic identity that should be accepted by users visiting your site. SSL/TLS uses digital certificates to provide authentication and encryption. To trust that a certificate is genuine and valid, it is digitally signed by a root certificate belonging to a trusted certificate authority (CA)”
SSL pinning is a security measure taken to reduce Man in the middle attacks it’s done for both Android and
ios applications , In general, Certificate Pinning is where you ignore that whole thing, and say trust this certificate only or perhaps trust only certificates signed by this certificate.
Android part
Now to break it or bypass anything we need to know how its build (i prefer learning slowly but conceptually)
Here is a blog that I found on how SSL pinning is implemented in Android.
It’s not that if you don’t know how it’s built you will not be able to crack it, but it will be easy to crack, if you know how to build it.
In
- Frida
- Objection
- Xposed Framework
- Manually changing the code.
Let’s move on step by step
1. SSL pinning bypass using Frida
Frida is a dynamic code instrumentation toolkit. It lets you inject snippets of JavaScript or your own library into native apps on Windows, macOS, GNU/Linux, iOS, Android, and QNX.
In general terms,
It helps in Injecting JavaScript to explore native apps on Windows, Mac, Linux, iOS and Android.
How can we use Frida to bypass SSL pinning in android?
Firstly you should install Frida from here for mobile & for a laptop, you can just use the command line.
$ pip install frida-toolsRequirements :
- Python 3
- Linux/Windows/Mac
- Rooted android device
Connect your device to adb command shell, once connected you can push the downloaded file to your data/local/imp folder.
$ adb root # required
$ adb push (path of the Frida file) /data/local/tmp(path to be saved) Now open Cmd/ Terminal & follow these steps,
$ adb shell "chmod 755 /data/local/tmp/frida-server"
$ adb shell "/data/local/tmp/frida-server &"If everything goes well we can make a quick check by running(this will show the processes running on device)
$ frida-ps -UYou will get something like,
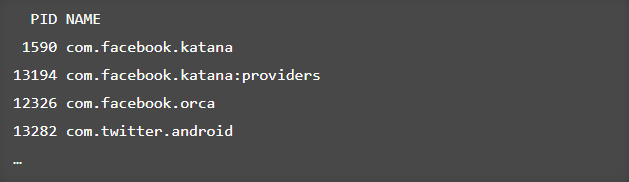
Here you need to have the
Once its done rename it’s
$ adb push (path of certificate) /data/local/tmpThe last part of Frida is your Javascript, you can write your own or copy it from here. Save it as a js file & run the command.
$ frida -U -f it.app.mobile -l frida-android-repinning.js --no-pause
Where
-U stands for "USB device"
-f stands for "Filename"
-l stands for "location of js file"
--no-pause stands for "automatically start main thread after startup"If everything goes well, you will get an output such as
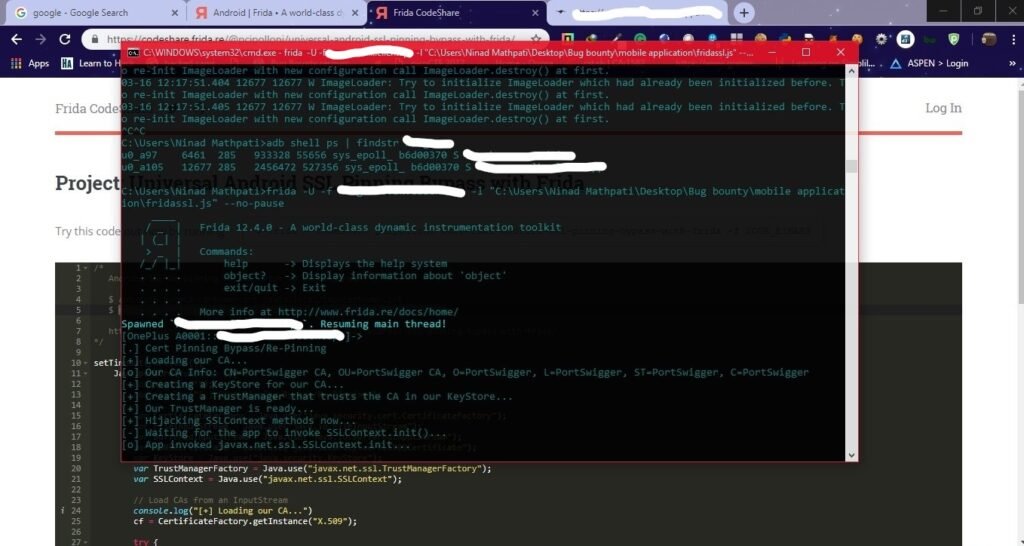
& bypass the SSL pinning.
Now, you are good to go, you can successfully intercept the requests and work on dynamic analysis. Some errors in this will be sometimes you won’t be able to bypass in
“Frida server service already running“
Here you need to kill that service using the adb kill command.
$ adb shell ps | Findstr Frida
$ adb kill ps(process id)This was all about Frida SSL bypass
Now let’s move towards Objection
2. SSL pinning bypass using Objection
You can install it by running
pip3 install objectionOnce done get your file name of the application by using Frida or adb.
$ Frida-ps -U
or
$ adb shell psthen,
objection patchapk -s com.xyz.android.apkThis will create a new
Push the
$ adb push <local file path> <remote file path>
or
$ adb install (path to apk)Now run,
objection -g (new apk file name) explore -q
Where,
-g stands for "Name of the Frida Gadget/Process to connect to"
explore stands for "objection exploration REPL"thus if the file is successfully injected
run "android sslpinning disable"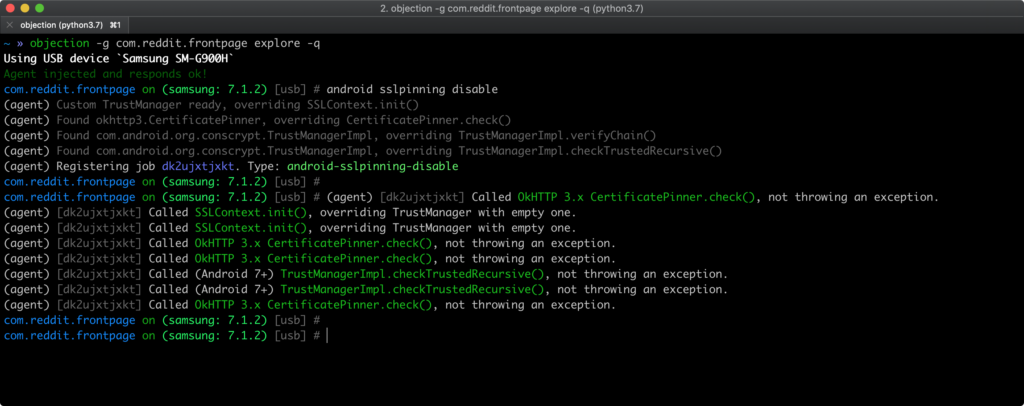
Now, you are good to go and intercept the requests through burpsuit.
3. SSL pinning bypass using Xposed framework
Xposed is a framework that allows users to easily apply add-ons (called Modules) to the ROM. Rather than flashing a new ROM to get a specific feature, you can use Xposed to add individual features to whatever ROM you’re using, or even just the stock ROM.
Installation,
Download the app from here
Run it and find an application named SSL pinning bypass, install it
you get a screen like
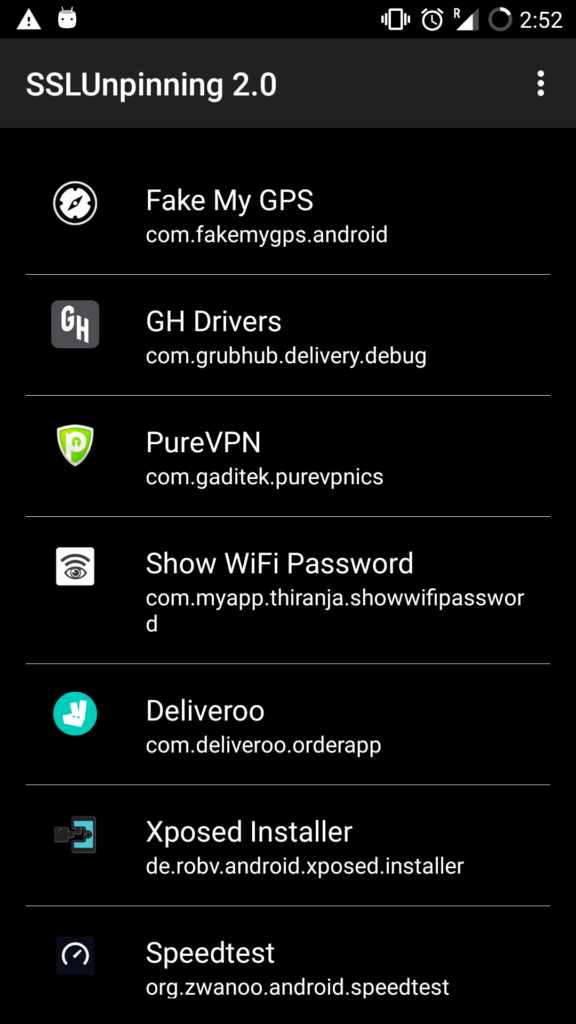
Thus click on whichever application you want to apply the SSL bypass & you are ready to go and intercept through burp request.
4. SSL pinning bypass through manually changing the code
The reason why I gave a link to SSL pinning implementation above is for this one, if none of the above methods works, this should work but it’s not simple, here you need to have knowledge about the android app structure how it’s built and how it works, sometimes a developer would choose to provide their own SSL libraries instead of relying on the system libraries to handle the SSL certificate validation. So here we can decompile the
Here you need to find the code responsible for certificate validation, once you get it you can manually fix it or by using Frida you can hook the application.
Here is an awesome blog which shows a
Thus, these were some methods to bypass SSL pinning in android.
iOS part
As I said we need to know the basics or
Let’s come back to bypass part, there are 4 ways to do that:
- Frida
- Objection
- External application (Cydia)
- By modifying the IPA file
Let’s move on step by step
1. SSL pinning bypass using Frida for iOS
As you know already about Frida, basically it’s just used for hooking the application.
Here basically we need to modify the application in runtime so that’s what Frida is used for, we can use Frida Gadget dynamic library to modify the application during run time, so what we will do is extract the IPA file then modify the binary to load Frida gadget, if we are changing or modifying the IPA file we need to code sign it for the IPA to work, code signing can be done by creating a developer account.
Once code signing is done repack the IPA and install the application.
Looks complicated? right!
Don’t worry objection is here to help you,
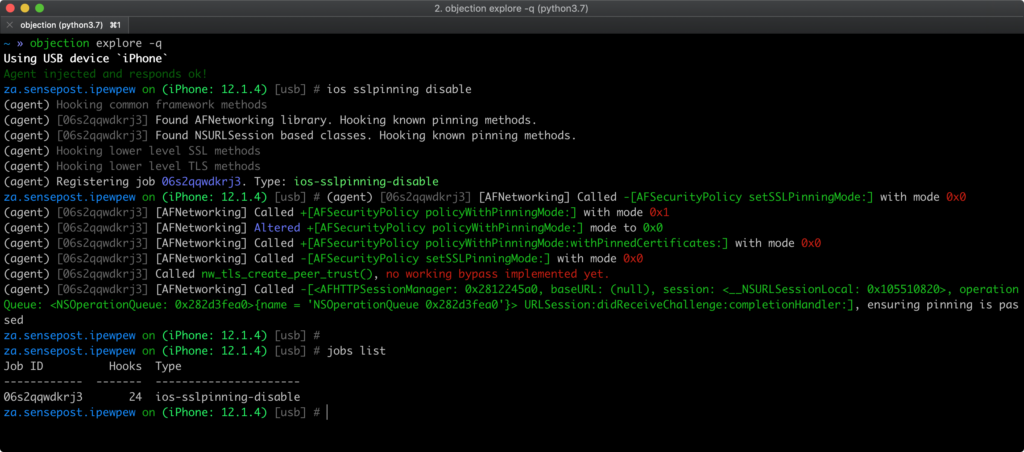
2. SSL pinning bypass using objection for iOS
Here it is simple as of android you need to install objection
then use the command,
$ objection patchipa -s test.IPA -c 0[REDACTED]C
-s stands for the path to IPA file and
-c stands for code-signing certificateOnce done, install the modified application through
3. Use of external application
There
So what is Cydia?
Cydia installer is a free third-party app installer which is developed for the iOS devices. Think of Apple’s official App Store, this is similar to the app store which means you can download apps, games from the Cydia downloader, but there are many other advanced options that have been included in the Cydia free store, which is more than the official store.
Thus, here you can find the “SSL killswitch“, install it and unpin the SSL for the application as you did it in android.
3. Modifying the IPA file
Most of the time the above methods should work. If not, this will definitely work, but here you need to know how the IPA application works, there is always an option to use disassemblers to be able to modify the IPA file to bypass any certificate validation. Some of the most common disassemblers are Hopper and IDA. Modifying the IPA will most likely break the signed application and it cannot be installed on an iOS device. Resigning the IPA file will allow you to install the mobile app.
That’s it for today. This was all about SSL pinning in
Hint for the next blog:- How critical is IDOR vulnerability ? Can it take down a whole company?
…. To be continued
Till then Happy hacking!


